Sharing Threat Intelligence (TI) between security and product vendors is an unmarked territory that has little to show from real word examples. Here we tell our story on how we embarked on a journey that resulted in a fruitful collaboration between WeTransfer and Microsoft that has a unique altruistic goal of protecting our users. Our collaboration introduces a new strategy in threat neutralization as we combine our knowledge and efforts in order to move the detection and mitigation of threats up in the attack Kill Chain.
Modern attacks aiming to steal user credentials or spread malware have evolved in a way that uses multiple platforms and applications to successfully deploy their campaigns. A real world example that we have come across lately is that attackers create a phishing PDF document or a Macro enabled document with malicious code and instead of sending it over to their victims directly via email, they create a transfer via WeTransfer. They expect that their malicious document will be opened by the recipient of the transfer via an Microsoft 365 account and they aim to steal the Microsoft 365 user credentials of the recipient by tricking them on clicking on misleading messages or alternatively to execute their malicious code which could result in a complete host compromise. To successfully deploy their attacks many preconditions need to be met and user interaction is needed.
Attackers often use techniques that will enable them to go undetected by some threat monitoring solutions. They deliberately mask their content as a transfer instead of dropping it as an attachment that would immediately trigger the defensive and monitoring mechanisms of the hosting providers. In this specific scenario, the attackers misuse the cloud infrastructure from WeTransfer and Microsoft in order to serve their malicious content to the end user. They also choose to delay the weaponization of their content in exchange for higher chances of executing their payload.
Based on the above attack scenarios that have become popular the past months, we started researching new ways of tackling these cross-platform attacks. A series of events that we describe later in this blog along with the luck of connecting with bright minds that aim to make our digital world a bit safer led us in establishing an information exchange service on Threat Intelligence (TI).
A bit of history
Back in January 2020 while analysing our application logs we noticed something pretty strange. We identified a set of IPs that were successfully accessing transfers belonging to a wide range of accounts that have no correlation between each other. In more detail, the first findings were pointing to 5 IP addresses that have completed 3357 downloads from a seemingly random set of Pro accounts and Free users during the last 30 days. The graph below presents the activity of those 5 IP addresses in the span of two weeks.
What gave us a good scare was that the vast majority of these requests were successful (200 OK) which means that this is not a brute force attack or a dictionary attack.

We lingered for some time with thoughts like, someone has reverse engineered the function for the creation of our public ids, or that the entropy of our shortURLs is not good enough (don't bother, we did the math for you and you have a chance of 1 in 400 billion to guess a valid shortURL). After taking a deep breath and analysing further the data that we had, we realised that the activity is not originating from malicious actors but from Microsoft. All IPs in question were attributed to Microsoft Azure locations. Manual testing led us to the conclusion that the specific service generating this traffic is Safelinks.
When a Microsoft 365 user receives messages with links to web pages, Safelinks checks whether the links are related to phishing scams or are likely to download viruses or malware onto your computer. A detonation service is used by Microsoft Defender for Office 365 to analyse file attachments (through the ATP Safe Attachments feature) and embedded links (through ATP Safe Links) in real-time within controlled environments and warn customers of unknown email threats if it detects any malicious behavior. Thus, all the activity described above is generated by SafeLinks that is engaged in order to protect the Microsoft 365 users receiving transfer links via WeTransfer.
Collaboration
We are aware that WeTransfer is occasionally used as a platform to share malicious or offensive content by bad actors. We highly respect users' privacy and we do not actively scan the content that the users upload in their transfers. However, we are actively monitoring malicious activity in our platform and in addition, in order to fulfil our moral responsibility to reduce the spread of Child Sexual Abuse Material (CSAM) we do use automated systems to detect such content. We always strive to protect our users and reduce the malicious or abusive content by constantly implementing new tools and services. Microsoft has the ability to identify hosting sources for the attacks they see on their customers. So in this case, Microsoft is actively analysing, via their Microsoft 365 users, content in our platform. We immediately saw an opportunity to create an ally in making WeTransfer a safer place. We reached out to them and we proposed to collaborate on a basis of sharing TI. There was a genuine interest to partner and join forces with the unique intention to protect our users, to more effectively neutralise attacks across platforms and make the Internet a safe place, even a tiny bit.
This collaboration would improve our cumulative velocity in neutralizing threats across cloud environments. For WeTransfer it would be beneficial as we would receive valuable information about malicious transfers in our platform on which we would be able to act upon and Microsoft would get some insight on the bad actors creating that content. Even if the information that we would share with Microsoft is only on metadata level, feeding TI indicators back to detection mechanisms is an efficient way to increase the quality of the findings and expand the capabilities of the protection mechanisms. For example, more sophisticated mechanisms aiming to hunt and identify activity of malicious groups can be developed.
Technical bits
The design of the solution to facilitate the information exchange between WeTransfer and Microsoft is actually pretty simple. The information is flowing from Microsoft to an EventHub from which we are ingesting in real time the "events" that in this case are JSON blobs that contain TI for a specific transfer.
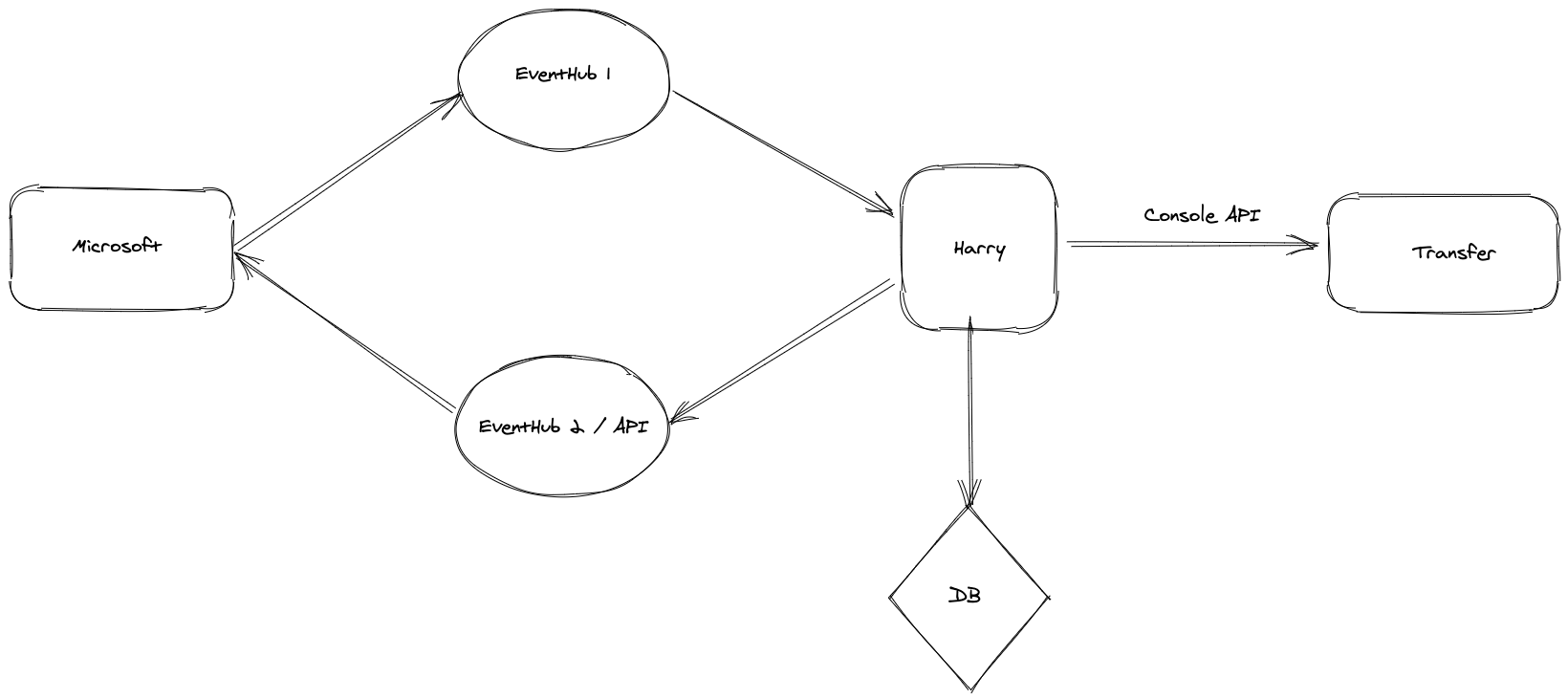
Our internal service (dubbed Harry) is subscribed to the EventHub and is always listening for new events. When a new report arrives, we extract the necessary fields such as the URL, the submission ID and the verdict (e.g. phishing, malware) from the report. Then we sanitise and process the URL to obtain the transfer public ID so that we can interact with our internal APIs.
For analytics purposes, as well as for post-processing operations, a database is created to store all blocking actions. The information stored in our DB is used to build test cases such as, identifying repeated offenders, flagging malicious content that is resurfacing or correlating events and IP addresses. This information enables us to react more effectively in security incidents and reach safe conclusions based on verified data.
On the performance side, we have managed to achieve something unique. The overall time to detect a link that contains malicious content and block it is less than 20 seconds. This includes availability of the TI from Microsoft, sharing the information to EventHub, retrieving the TI and applying the block on our side. Apart from the short turnaround time from Microsoft's Detonation service in the Safelinks solution, the fact that we trust the accuracy of the TI that we receive from Microsoft allows us to exclude manual verification of the samples arriving with a flag of high confidence and block them immediately.
The additional logic that we have developed in our service has allowed us to use the TI provided by Microsoft to hunt for malicious content and offenders in a much wider scope in our platform. Based on the metadata of the flagged transfers as well as on sender metadata we can block transfers that are sent not only to Microsoft 365 users but also to any Email Service Provider(ESP). We are also able to flag repeated offenders or malicious files that have been widely shared.
Results
The internal service has been running successfully for a few months now and it is evident that proactively tackling abuse across platforms has tangible results. The collaboration with Microsoft has helped us in blocking a considerable amount of malicious transfers and has resulted in a stable downward trend in abuse overall.
The threat intelligence that we receive is classified either as malware or phishing. The TI is equally split between these two categories. This gives a good indication of the nature of the malicious attacks happening via our platform. Some typical cases of the detected malicious content are presented below.
Transfer containing a phishing PDF file:
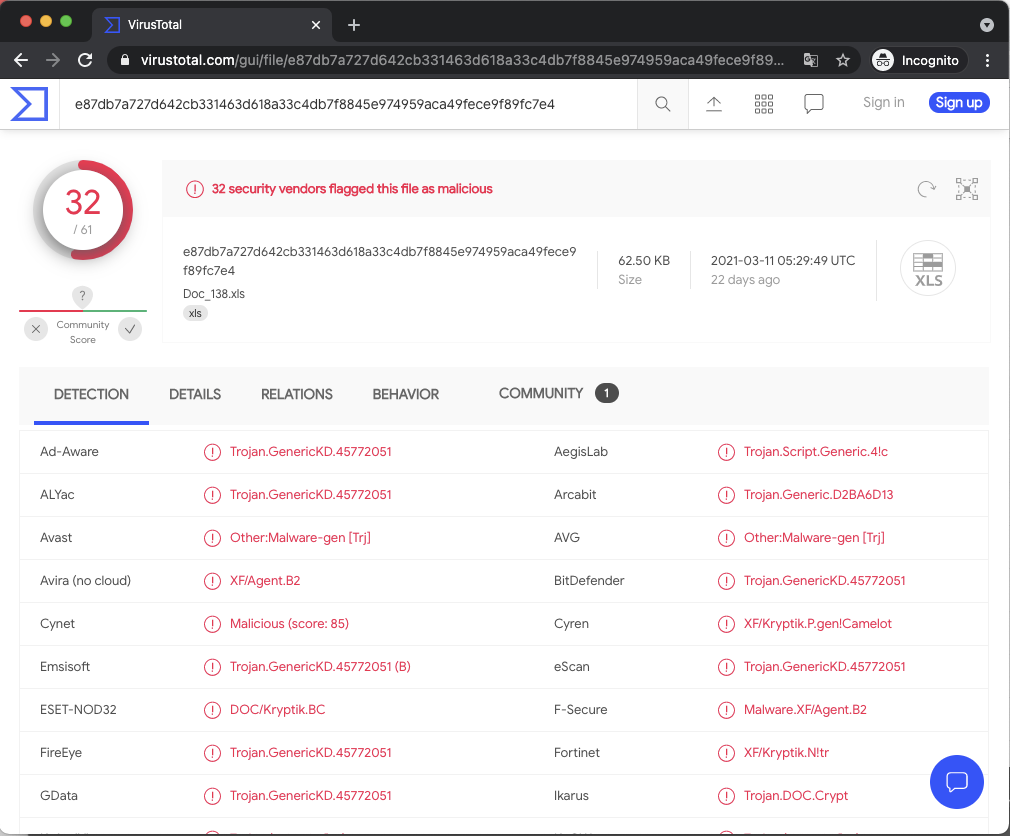
Malicious XLS file contained in a transfer:
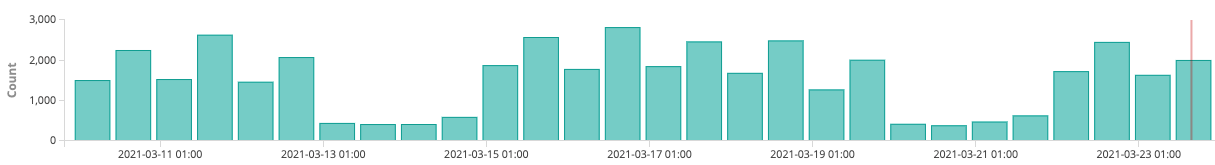
The service has proven itself capable of also detecting widespread phishing campaigns misusing the WeTransfer platform that amongst other users, target Microsoft 365 users. The graph below demonstrates such an example where we noticed a spike of events flagging an increased number of transfers as malicious:
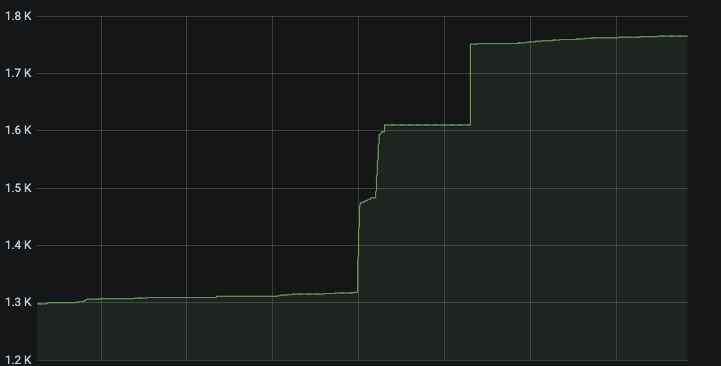
This spike was linked to a sophisticated attack that attempted to abuse our platform in order to send out approximately 6000 transfers with malicious content in a short period of time. Our information exchange service acted as an additional pointer to reveal this attack. By combining this alert with other defensive mechanisms that we have in place, we were able to counter this attack and move forward with the remediation process. In total, 5913 transfers were blocked and 2986 accounts associated with these transfers were deleted to further ensure that they will not be used to deploy a similar attack.
Looking ahead
Our information exchange service would not be complete without sharing metadata with Microsoft, linked to the malicious actors and based on the TI that we receive. In particular, WeTransfer will be sending back to Microsoft limited information related to the creators of the malicious transfers which will be then used to deepen the knowledge and the capabilities of the detection mechanisms developed internally at Microsoft. This part is not yet implemented but will soon be deployed so that both parties can equally benefit from this collaboration.
The next step in our venture to make our products safer and free of abuse, apart from adding logic to our service as described above, would be to enhance the TI sources that our services consume. We are actively seeking for more collaborations that would work in a beneficial way both for WeTransfer and the vendors that would be willing to build such a relationship. We are delighted that this collaboration with Microsoft enables us to create safer products for our users and at the same time helps our partners to make the Internet a safer place.